Ubyon blog
by Harsha Nagaraja on
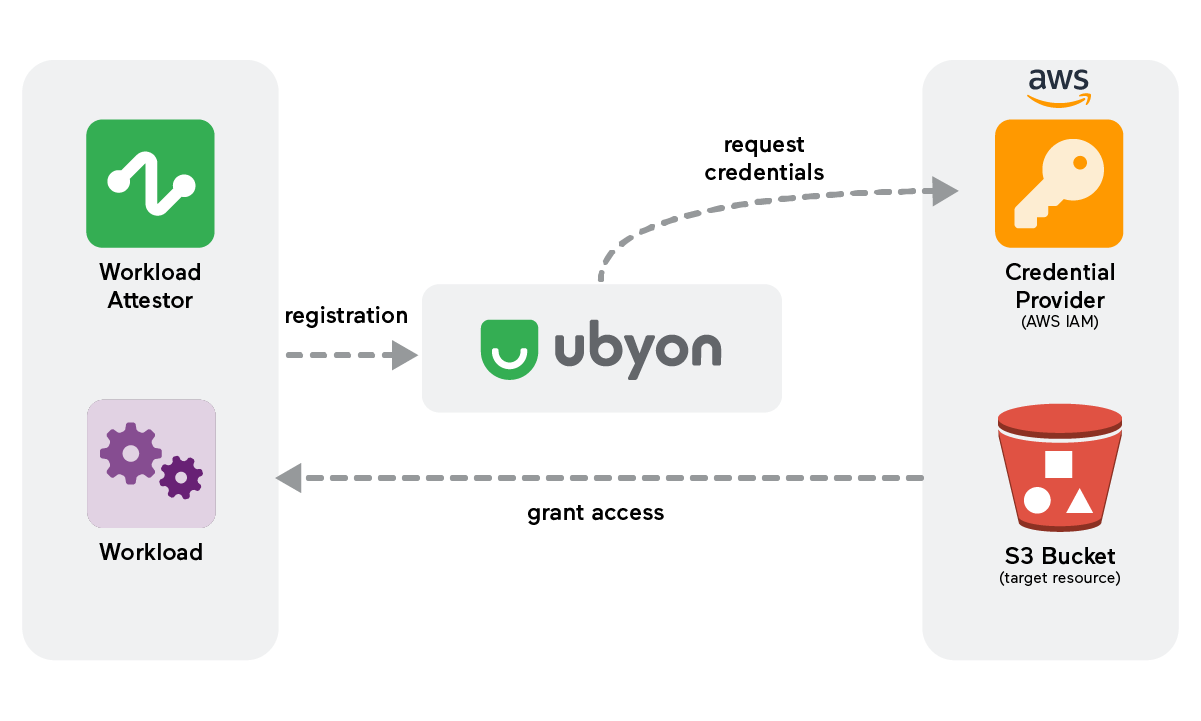
Workloads access overview with Ubyon
This outlines Ubyon's solutions for securing access between workloads and resources.
by Ramanan Subramanian on
The Emerging World of Workload IAM
In the era of cloud computing, the proliferation of non-human identities has been remarkable. Businesses increasingly rely on software workloads like applications, services, and scripts, necessitating unique identities for accessing cloud resources.
by Saleh Noordeen on
Viewing IDP-based application entitlements with Ubyon
Admins can view granular details for the groups, users, and hooks associated with applications using IDP attributes like cost center or department.
by Saleh Noordeen on
SSO for applications with Enterprise IdPs
Our latest update brings seamless Single Sign-On (SSO) integration for applications with Enterprise IdPs.
by Saleh Noordeen on
JIRA integration for just-in-time access
An example of just in time access using Jira.
by Saleh Noordeen on
Just-in-time access with Microsoft Teams
This demonstrates securing access with Ubyon and Microsoft Teams.
by Ramanan Subramanian on
Ubyon: Converged Access Management Platform
Ubyon’s architecture combines cloud access management and governance with approval workflows.
by Saleh Noordeen on
Integration with Databricks
This demonstrates securing access to Databricks with Ubyon.
by Saleh Noordeen on
Least privilege access with Ubyon
An overview and demo of least privilege access with Ubyon.
by Saleh Noordeen on
Just-in-time RDS access with Ubyon
Just-in-time access to an AWS RDS database with Ubyon.
by Saleh Noordeen on
Cloud access simplified with Ubyon
An example of a user requesting time-limited access to S3 buckets in AWS.
by Saleh Noordeen on
Unify Kubernetes access with Ubyon. (Video)
Manage and access Kubernetes clusters across multiple environments with Ubyon.
by Saleh Noordeen on
Just-in-time Remote Desktop access with Ubyon
This demonstrates RDP server access with Ubyon LaunchPad.
by Ramanan Subramanian on
Easy and secure SSH with Ubyon Link
With Ubyon Link, developers don’t need to change their SSH workflows.
by Saleh Noordeen on
Ubyon Launchpad unifies access to private resources. (Video)
Protect resources with Ubyon TrustMesh without private networks or VPNs.
by Saleh Noordeen on
On-call integration with Ubyon. (Video)
This demonstrates on-call integration with Ubyon and PagerDuty schedules.
by Saleh Noordeen on
Just-in-time RDS access with Ubyon
Just-in-time access to an RDS MySQL database with Ubyon.
by Ramanan Subramanian on
Scaling least-privilege access with Converged Access Management
The rise in hybrid work and the move to Cloud and SaaS has led to “converging” several access management functions into integrated solutions.
by Saleh Noordeen on
Just-in-time Snowflake access with Ubyon
This demonstrates just-in-time access to a PaaS application, Snowflake with Ubyon LaunchPad.
by Saleh Noordeen on
Modernize SSH multi-cloud access. (Video)
Ubyon streamlines SSH workflows and makes administration more straightforward.
by Ramanan Subramanian on
Ubyon Launchpad brings all private resources together.
With Ubyon Launchpad and TrustMesh, resources can be protected without private networks or cumbersome VPN clients.
by Saleh Noordeen on
Just-in-time VNC access with Ubyon
This demonstrates just-in-time access to a VNC server Ubyon LaunchPad.
by Saleh Noordeen on
Ubyon: Identity as a service for applications
An example of using Ubyon to provide identity to applications.
by Ramanan Subramanian on
Unify Kubernetes Access Across all your Application Environments
Ubyon simplifies the management of access to multiple Kubernetes clusters.