Ubyon: Converged Access Management Platform
The shift to cloud, PaaS, and SaaS has outpaced traditional Identity Access Management and Governance and Privileged Access Management, which struggle to manage access across diverse environments. These conventional solutions are ill-equipped for the dynamic access needs of both human users and automated workloads. Ubyon is built to surmount these challenges, offering a robust framework that merges cloud access management with security governance. By harnessing Slack and MS Teams for streamlined approval processes, Ubyon enables organizations to manage access rights across multi-layered environments, thereby enhancing security and averting potential credential compromises.
The problem
Ubyon was developed to tackle prevalent access management challenges by offering a "Converged Access Management" (CAM) solution, extending its comprehensive coverage to include not only human users but also workloads (scripts and services). At its core, Ubyon features TrustCore, an API-integration and orchestration service that is delivered as SaaS, coupled with TrustMesh, a multi-cloud, cloud-native proxy that is identity and resource-aware that is delivered as SaaS or hosted on the customer’s premise. This solution natively integrates a governance policy framework that facilitates decentralized administration of access rights for users and workloads alike, adhering to the least privilege principle and streamlining the management of credentials. Ubyon's approach ensures a superior user experience across the board, benefiting end users, SRE/DevOps, and security teams.
We take a representative example to highlight a typical use case of a user accessing a data source. This use case outlines the end-user challenges and sheds light on the various access products the security team deals with to satisfy a basic resource request.

- The end user needs a single entry point to find and request access to resources, requiring them to follow manual processes to locate resources.
- The user makes a request through a ticketing system, which is onerous for Just-in-Time and routine accesses.
- Once granted access, VPNs are required to connect to private network domains. Users are required to know which cloud/network domain to connect to to access the appropriate resource.
- Traditionally, VPNs and firewalls implement coarse-grain ACLs that invariably allow permissive access. The problem gets worse in cloud environments where resources are dynamically provisioned. Users connecting to cloud networks can gain access to multiple classes of resources.
- To access a resource, users need to obtain access credentials. For instance, a username/password is required to access a database. This can be retrieved by accessing secret stores through a privileged access management process, which entails additional steps burdening users and administrators.
- Security and product teams have to manage these siloed access products, making it a challenge to monitor, secure, and adopt a practice of least and zero-standing privilege access that can scale with ease.
While this example highlights the challenge of accessing a database instance, this problem extends to several classes of resources, such as:
- Cloud Provider managed: resources managed by cloud service providers, e.g., AWS instances, AWS EKS, AWS RDS, GCP GKE, GCP BigQuery, Azure SQL, etc.
- PaaS managed: resources managed by PaaS platforms, e.g., Snowflake, Databricks, etc.
- Enterprise managed: resources directly managed by the enterprise IT or SRE/DevOps teams, e.g., VMs, machines, Kubernetes clusters, databases, etc.
- Identity providers: identity providers that federate with multiple external apps and platforms, e.g., Okta, Google Workspaces, Azure AD, etc.
The Solution
Ubyon was built to address these challenges by delivering a “Converged Access Management” (CAM) solution. Ubyon’s SaaS-delivered cloud access management solution is developed using a foundational API-enabled authorization service (TrustCore) and a multi-cloud, cloud-native, Identity-aware, and resource-aware proxy (TrustMesh). The solution natively integrates a governance policy framework that promotes decentralized administration of least-privilege access with automated credential management. All this is achieved while ensuring a great user experience for end users, SRE/DevOps, and security teams.
To better describe the benefit of such an approach, let us consider the previous example with Ubyon and walk through the access journey experienced. It becomes evident from the start that the solution offers an integrated experience that avoids multiple touch-points across various access products.
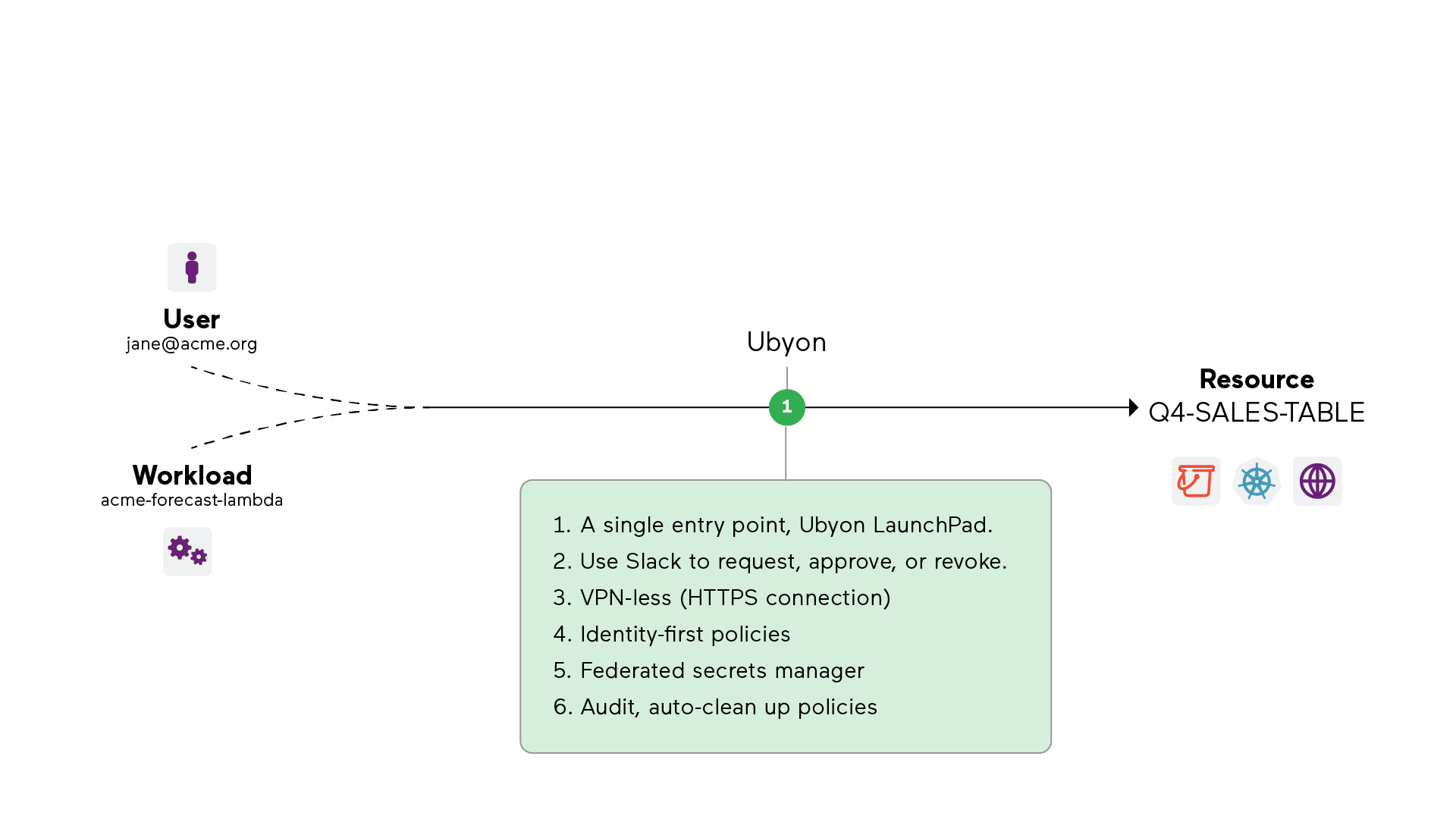
For End-users:
End users have one place to access all their resources - a “launchpad” web page to find, locate, and request access to any resource. They request access to a resource with Slack (or MS Teams) or directly from Launchpad, removing the burdens of using cumbersome ticketing systems. Users can view all their resources, including the database instances, through the web portal or directly from their terminal CLI and connect to them without the burden of VPNs or manual credential management.
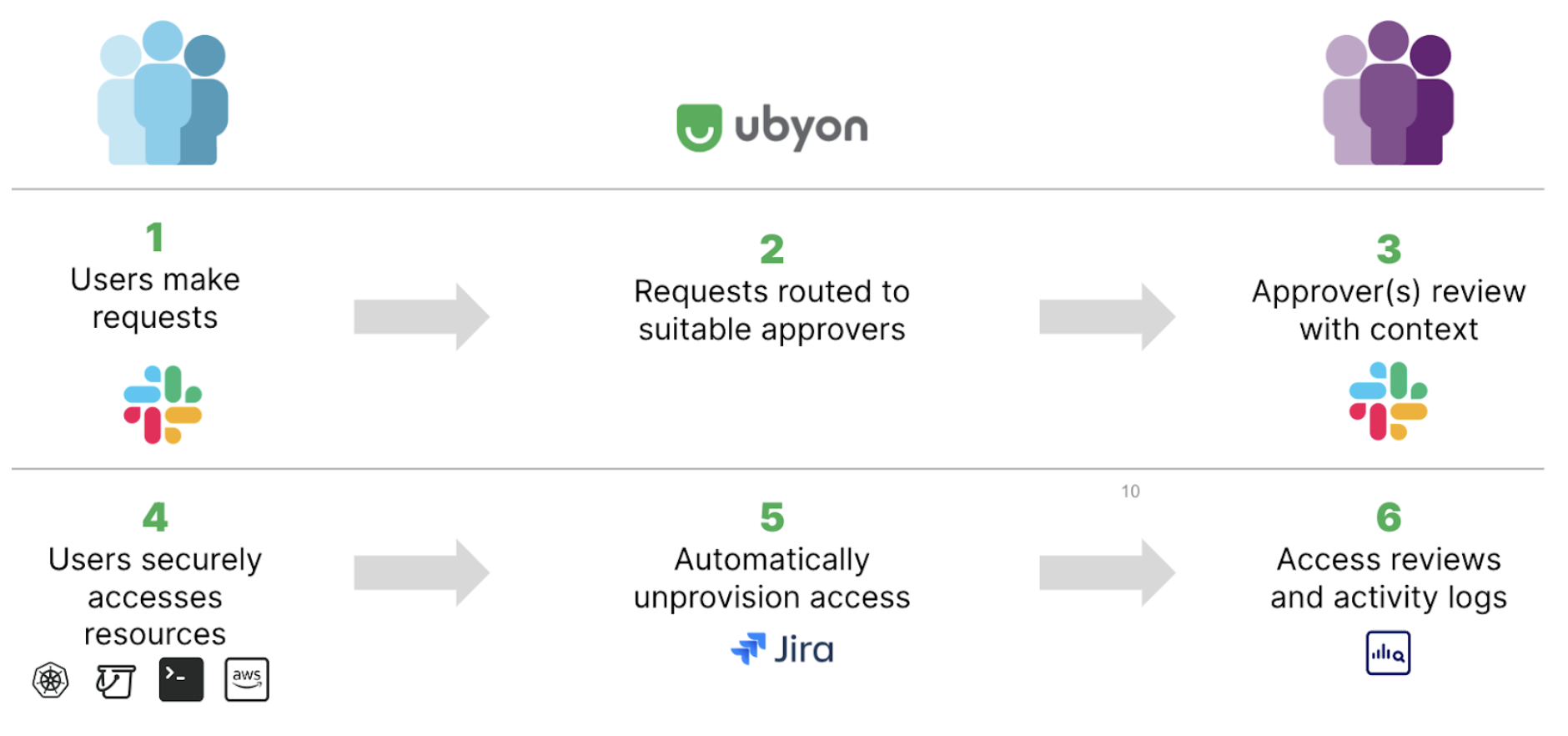
For Security teams
By implementing Just-in-Time access with decentralized administration across all resources, security teams can unify security governance and enhance their security operational efficiency by empowering different team leaders to handle approvals of resource requests. Security admins, who were bottlenecked or overwhelmed in the approval chain in the past, can unblock themselves and delegate approval responsibilities to other leaders based on organization or project scope. The lack of decentralization results in hurried approvals without thorough evaluations, resulting in the inadvertent granting of excessive user privileges and the unintended exposure of long-term credentials or frustrating the software worker due to delays in the approval process. With Ubyon’s cloud access management with integrated governance, security teams can significantly reduce the attack surface and prevent credential breaches through the automation of credential management. Such an approach delivers comprehensive visibility that encompasses the entire access lifecycle, from access reviews to audits conducted at the session level. Comprehensive visibility is pivotal in expediting incidence response and compliance procedures across all operational environments.
The Ubyon stack
Ubyon provides an identity-first cloud access management solution with fine-grain access controls managed through Just-In-Time access workflows for all resources across heterogeneous and distributed environments. The framework extends naturally to headless users, such as scripts, ensuring all access is secured. The result is an empowered cloud operations teams that move with agility while providing secure and compliant access guardrails. The solution consists of three core components that work in conjunction.
| Component | Customer needs |
|---|---|
| Cloud Console: configure access and review corresponding logs at a session level. | Do I have visibility for compliance and audits? Can I view and right-size permissions? |
| TrustMesh: Secure VPN-less connectivity with automated and integrated secrets store management. | Are resources accessed securely? Are credentials distributed securely? Are credentials long or short term? |
| TrustCore: Federated, just-in-time access to cloud, PaaS, and SaaS with robust API and ITSM integration. | Who has access to prod, PaaS, etc? Is access right-sized and just-in-time? |
While there are several available open-source and commercial proxy solutions, most of them have not been built for cloud access management. Security teams have struggled with resilient proxy deployments across hybrid cloud environments, configuring cloud resources that tend to be dynamic in nautre, managing fine-grained access policies to offer least-privilege access, and scaling operations to the wider organization.
Ubyon’s cloud access management solution offers a rich governance policy engine to automatically administer dynamic access policies to discover resources and protect them with Just-in-Time access.
- Discover: Eliminate the overheads of configuration management and automate policies with Ubyon’s capability to discover your cloud resources, such as AWS RDS instances, AWS EKS clusters, IAM roles, machines, S3 buckets, and Kubernetes services.
- Just-in-Time access: Time-bound policies combined with automatic credential management dramatically reduce the attack surface and prevent credential breaches. The security team can easily delegate request approvals to specific team leaders, thereby scaling operations while realizing the least privileged access.
- Easy administration: Ubyon’s Cloud Console offers a single place to administer and manage the Ubyon infrastructure, manage principals and resources, define policies, and audit every access that can be tracked at a session granularity. The solution provides a choice to either consume TrustMesh “as-a-service” or deploy it in the enterprise cloud or on-premises environment.
Solution Components
Looking under the hood of the Ubyon black box, the following components can be seen working together to deliver the solution.
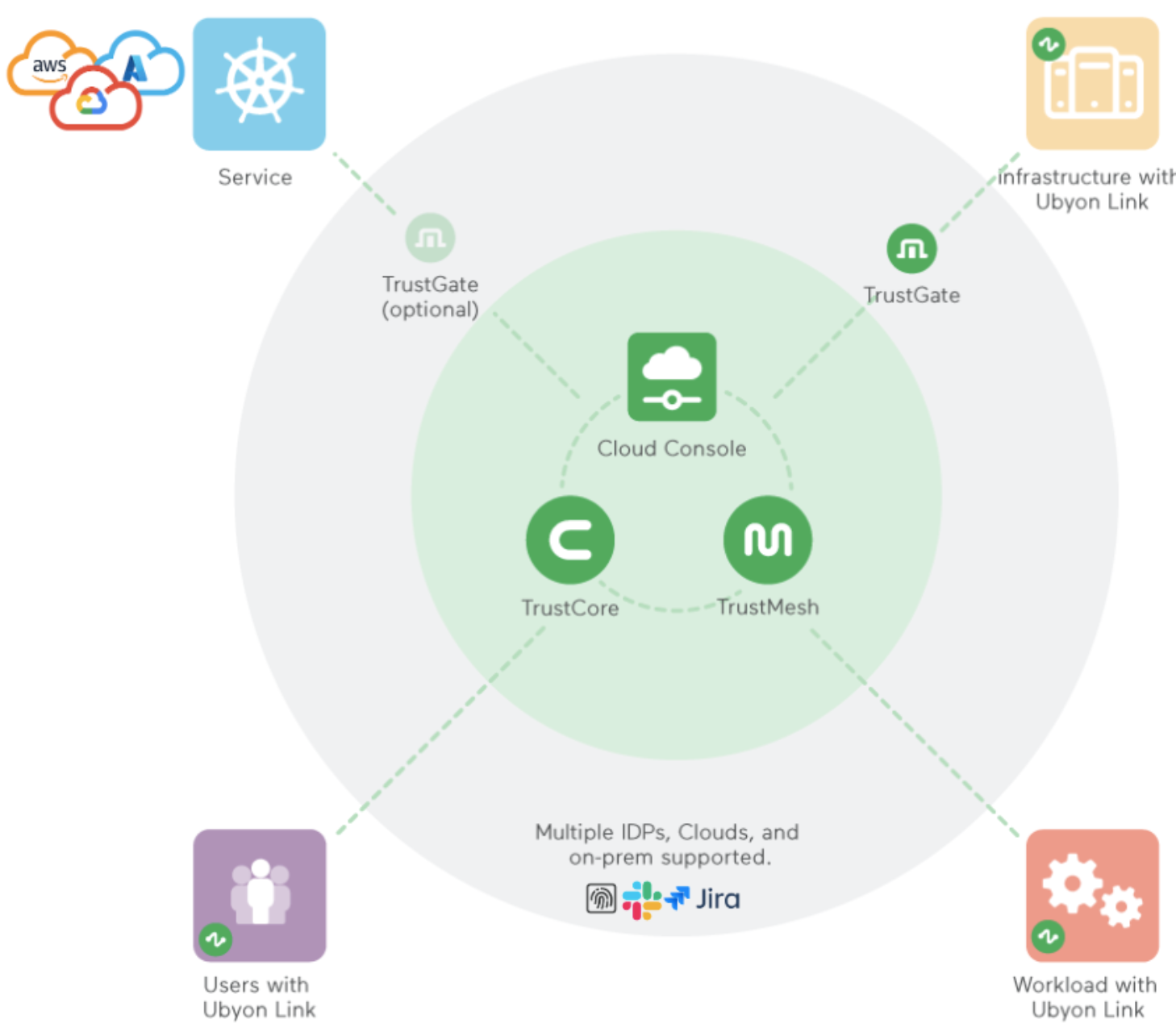
- Target Resources: Ubyon is designed to cover all resources (privileged or otherwise) deployed in the public cloud-managed, enterprise-managed public cloud and hybrid cloud environments.
- Principals: A principal can be an interactive user/person or a headless user (script/workload).
- Cloud Console: Centralize the administration of Ubyon infrastructure. With multiple distinct user types, such as Administrators, Approvers, and Users, Ubyon offers a tailored experience to the platform. Administrators have full access to the Ubyon Cloud Console. At the same time, approvers and users are granted access to the Ubyon Developer Launchpad, which offers unified access to all resources the user is authorized to access.
- TrustCore: TrustCore is an orchestration / API-Integration engine that talks to external services. TrustCore can be extended to integrate with any public cloud provider, such as AWS, GCP, or Azure, identity systems (such as Okta, Google, GitHub, AzureAD), PaaS, and SaaS services. The objective of these integrations is to be able to orchestrate a set of actions that grant temporary privileges to principals.
- TrustMesh: A cloud-native identity-aware proxy service that allows Ubyon to intermediate access to private resources, whether they reside in the cloud or on-premises. Enforcement within TrustMesh is implemented by this set of cooperating nodes - TrustGates. A TrustGate is a network gateway with fully automated zero-trust access, zone-aware high availability, and auto-scaling capabilities.
- TrustLink: These are connectors or micro-agents that allow users, machines, and workloads to connect to the TrustMesh and bridge a secure communication channel across firewalled networks. TrustLink is not required for all use cases. For instance, a user accessing their AWS console through Ubyon wouldn’t need the use of TrustLink.
Putting it all together: Database Access
Taking the earlier example, we can now visualize the user flow. Ubyon brings together Slack-based workflows, federating auto-expiring credentials with cloud providers (e.g., AWS), providing a VPN-less secure connectivity to the database resource, enforcing fine-grain access policies, and providing comprehensive visibility.
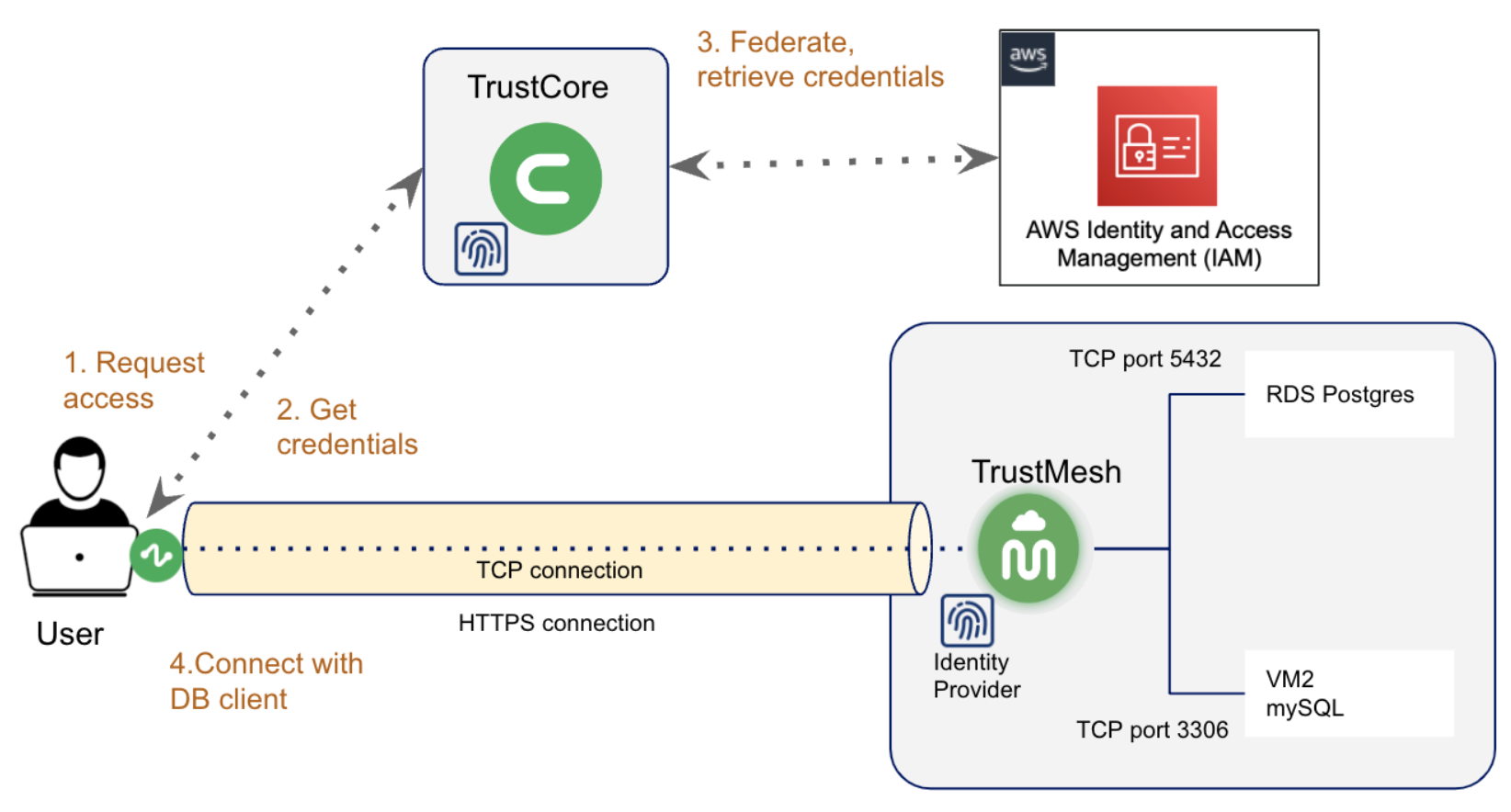
- The user makes a request to access the AWS RDS database instance through Slack. Based on the request parameters, on-call status, and user privileges, Ubyon TrustCore determines if the request can be approved or routed for explicit approval to a set of designated approvers.
- Once approved, the user can retrieve temporary credentials through Ubyon, which in turn federates with AWS and retrieves temporary credentials on behalf of the user.
- Using temporary credentials, the user can use their favorite database client to connect through Ubyon’s TrustMesh identity-aware proxy to the AWS RDS database instance.
To access the database instance, the user can execute a Ubyon CLI command to (1) get the necessary credentials based on the role and database username and (2) securely connect to the private database instance.
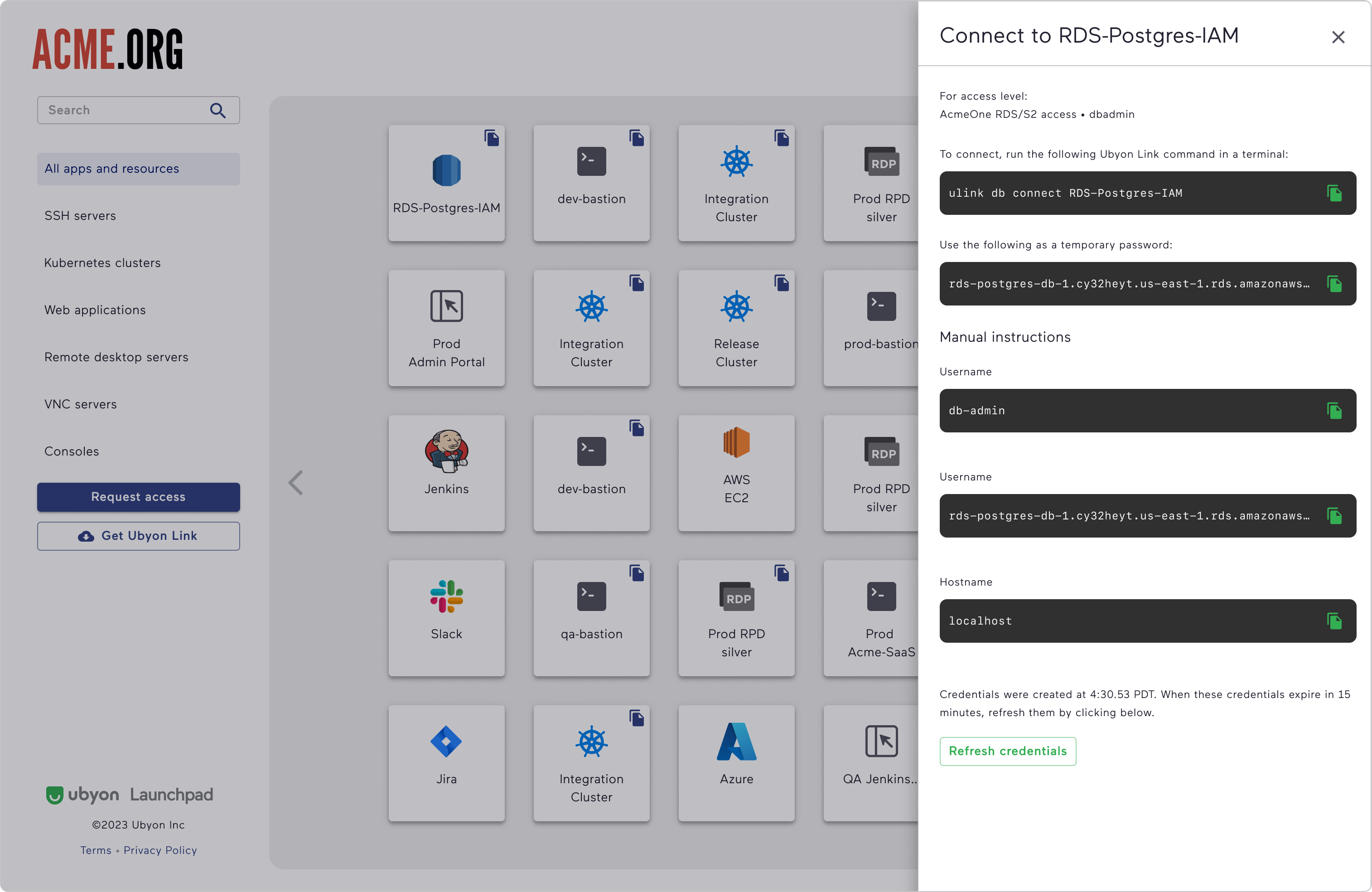
Behind the scenes, all the complexity associated with federating with AWS, implementing Slack-based JIT workflows, retrieving and renewing temporary credentials, and connecting with Ubyon’s identity-aware proxy is hidden from the users. For the user, it feels like connecting directly to the resource. Administrators can leverage the power of the cloud IAM systems while reducing the IAM management complexity and deploying a “credentialless” infrastructure.
Comprehensive coverage
While cloud adoption continues to grow, the reality is that organizations need to manage access to both resources that they manage (such as VMs, internal web services, and on-premise servers) and to resources that are managed by IaaS/PaaS vendors (such as AWS RDS, AWS S3, Snowflake, and Databricks). To lower operational costs, there is a strong requirement to unify the administration and access these resources with uniform governance policies. This allows teams to streamline access with a single access solution - users have a simple and easy way to access resources, and security teams have a unified solution to administer access policies and manage audits.
Ubyon supports access to both “enterprise-managed” and “cloud-managed” resources. Teams can use the same Slack-based workflows to request access an on-premises web server or access an AWS RDS instance. Security teams can unify administration, policies, and audits for all resource access. In the case of cloud-managed resources, Ubyon federates with the cloud providers (IaaS and PaaS providers) to enforce access policies on behalf of the principal. TrustMesh can be introduced on-a-need-to-basis to provide an added layer of security to ensure that resources are kept private and not exposed to the public Internet and to derive deeper transactional visibility with fine-grain access controls.
| Feature | Enterprise managed | CSP managed |
|---|---|---|
| Resource | VMs, K8S, ... | EC2, EKS, GKE, ... |
| Permissions | Auto-expiring and persistent, fine-grained access natively managed by Ubyon | Auto-expiring and persistent, fine-grained access federated by Ubyon |
| Developer Access | Personalized, single-point of access with Ubyon Launchpad. CLI access | Personalized, single-point of access with Ubyon Launchpad. CLI access |
| Access path | TrustMesh is required | TrustMesh is optional |
| Access path | Managed from Ubyon's Cloud Console | Managed from Ubyon's Cloud Console |
| Access forensics | Access reviews. Protocol-level visibility in Ubyon logs. | Access reviews. Access-level visibility in Ubyon logs. |
Coverage of key use cases
Not all resources are created equal. Resources in production environments, where there is considerable access scrutiny, require tighter controls and audits. While resources in dev/pre-prod environments require frictionless access. In practice, access patterns tend to be far more diverse. In an attempt to categorize common patterns, we classify them under these topics.
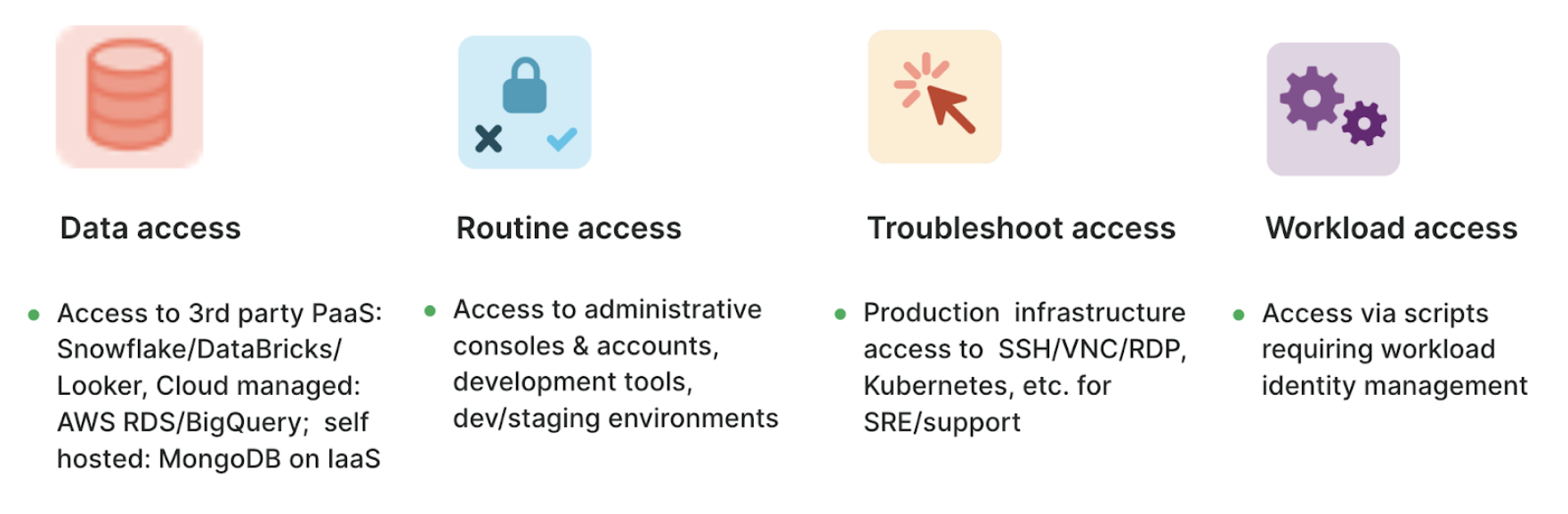
Traditional PAM focused on access for troubleshooting, where SRE/DevOps needed to typically SSH to a machine to deploy or debug issues. While this is still a relevant use case, we observe data access and routine access rapidly growing, with workload access looming in the background. These access patterns are different from the traditional troubleshooting access patterns.
- Data access: The rise of data science and ML/AI has resulted in unprecedented growth in frequent access to production data, training data, or specialized data sets.
- Routine access: As dev environments and pipelines adopt more cloud services, there is a greater need for operational controls and security governance.
- Workload access: An increasing number of tasks are being automated by scripts that access privileged resources. Security teams have limited visibility or controls to manage access made by these “workloads.”
Traditional PAM products were not built to address these use cases. Ubyon was built to address these use cases. The solution extends to cover users and workloads, providing an identity-first approach to access management.
Summary: Drive adoption of least-privilege access
Ubyon’s Converged Access Management allows organizations to adopt and scale least-privilege permission across all Cloud, PaaS, SaaS, and on-premises environments.
- Drive adoption by providing automated guardrails with great user experience, avoiding excessive permission requests. Start small with one team or one environment and then scale operations over time.
- Right-size permissions and grant access with Just-in-Time access workflows that don’t burden your teams. This practice reduces the potential blast radius of attacks and any credential leaks. Apply more scrutiny when reviewing permissions that applications request and deciding whether to grant permissions.
- Stop the spread by ensuring attackers cannot use excessive privileges to gain further access. When a principal asks for unnecessary permissions, it will be least likely to receive approval or be denied altogether. The best way to control damage is to prevent attackers from gaining elevated privilege that increases the scope of the compromise.
- Speed up compliance of SOC, SOX, PCI, and other compliance standards with detailed visibility from access reviews to access and audit logs that capture all access activity.
Striking the right balance between security and seamless engagement poses a significant challenge for organizations. But the right access management solution can help. Ubyon delivers a Converged Access Management (CAM) is a crucial component that consolidates and simplifies access across diverse environments while maintaining robust security measures, ensuring the realization of least-privileged access.